NAT Flooding: What It Is & How It Works
NAT stands for Network Address Translation. NAT provides 2 main duties.
The first duty is that it allows the translation of one (external) IP address to multiple (internal) IP addresses, which allows you to use more than 1 device through an Internet connection utilizing only 1 IP.
The second task that NAT performs relates to security, where it will normally only allow incoming traffic if it has been requested, so incoming unsolicited data will be ignored, and this process uses the NAT table (translation table) too keep track of the requests to know what to allow in.

NAT flooding, or NAT table flooding is where the maximum number of connections or table entries is used up, and there is no more room to add further entries. The NAT table is used to track requests for data and route the data appropriately. When you click to pull up a webpage like Google, as the data request is sent to Google, the NAT table gets an entry about this request that logs: the computer that asked for it, the port it was requested on, where it was requested from, and the amount of time to keep this request alive (timeout). When the data comes back from Google after the request, it references this to the NAT table to route the data back from which it was requested.
If data coming from the internet does not have a NAT table entry, then that data is simply dropped, as there is no record that it was requested, and this goes a long way to keep your devices free from unrequested attacks from the internet.
If the NAT table is full, then the data will still come and go, but with no room to create the entry in the table, the incoming data will be dropped as an unrequested connection. The NAT table in the radio (device mounted on roof by MCSnet for the internet) uses has 2048 ports it can use at a time, so NAT flooding is normally very rare except in a couple of cases. NAT flooding through a router is also possible and is one of the reason why your router might ‘hang’. The maximum number of connections supported by a router varies among different brands and models. Port forwarding and the DMZ (de-militarized zone) are protocols to allow some or all unrequested packets to a specified device.
Typical causes of NAT table flooding. The most common case of NAT flooding is peer to peer file sharing, where the file sharing program tries to connect to hundreds or thousands of other devices simultaneously. The fix to prevent NAT flooding while using a file sharing program is to limit the number of simultaneous connections, usually a couple hundred is sufficient. Another option, that is not usually available, is to set the timeout on open connections to a lower number, the default is normally 1440 minutes (24 hours), which means that the NAT table will wait up to 24 hours for the data before dropping the entry and feeing up the table entry. Viruses and other infections like botnets can also cause flooding, and the obvious fix here is to clean the infection or reload the software on the infected device.
Example: Adjusting Number of Connections used by utorrent
utorrent is currently the most popular bit torrent client. This shows how to fix the number of connections setting to help avoid NAT flooding issues.
- At the top, click on the Options menu item.
- Select, ‘Preferences’

- In the window that appears, on the left hand panel select ‘Bandwidth’
- Change the ‘Global maximum number of connections’ entry to 100 or less
- Click ‘Apply’

This same setting can be found in other popular clients like ‘Bit Torrent’ and ‘Vuze.’
Internet Configuration of the Router
- Open your web browser
(Internet Explorer for most systems, but we recommend using Firefox). - Enter 192.168.1.1 in the address bar near the top and hit Enter

- Use a blank username and admin for the password
(this is the default login, if you have changed the password, then use the one you have setup) - Under Setup -> Basic Setup
- Set the connection type as Automatic Configuration – DHCP and click Save Settings

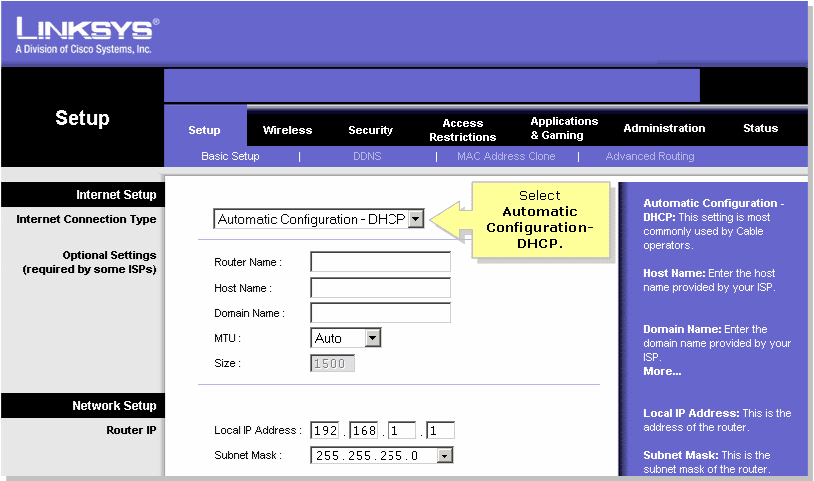
This is the factory setting of the router, so this step is not needed unless the router is configured incorrectly. If you are stuck on the password step and have forgotten your password, you will need to factory reset the router to fix this, which is done by 

Enabling Wireless Encryption
Internet Configuration of the Router
- Open your web browser
(Internet Explorer for most systems, but we recommend using Firefox). - Enter 192.168.1.1 in the address bar near the top and hit Enter


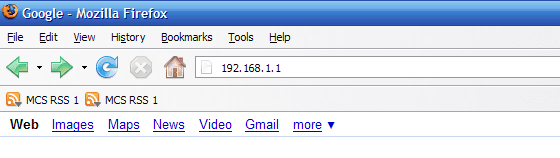
- Use a blank username and admin for the password
- Click on Wireless -> Wireless Security
- select WPA Personal as the Security Mode

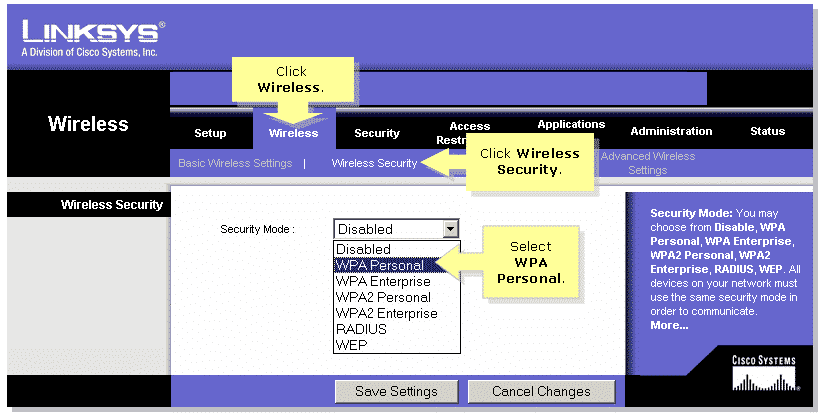
- Select TKIP
- Enter your desired network key
- Click Save Settings to save your changes.

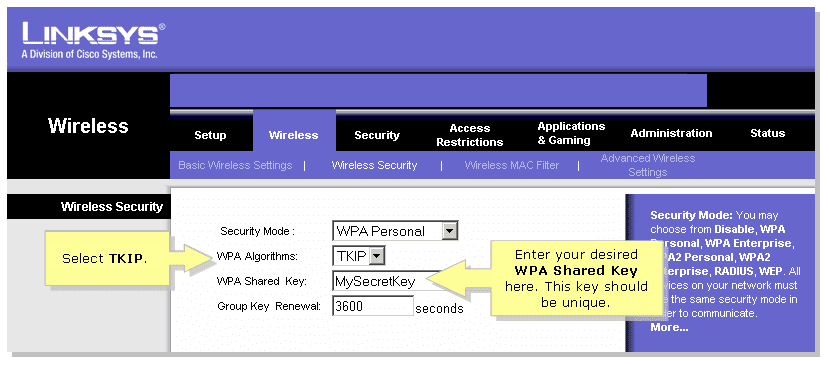
It is recommended to change the Wireless Network Name (SSID) at the same time you change the Wi-Fi password, this helps your devices recognize the change and avoids the issue where they try to use a previously saved setting instead of asking for the new password to connect. You can change the SSID in the ‘Basic Wireless Settings’ area.
Stay Connected With Us
Learn all about the latest tech, get helpful internet tips and hear stories from the talented people at MCSnet.


Let’s Talk!
Have questions about your internet? Need to troubleshoot a connection issue? We’re happy to help. Our team will respond within one business day.



Connect your rural home now


